uBlock origin
The best info filter!
- It's a browser extension, only supported by Chrome and Firefox
- It's better than other "adblockers" in many ways
- https://github.com/gorhill/uBlock/wiki/Overview-of-uBlock's-network-filtering-engine
- Works for elements in iframes as well, write rules regarding the domain of the iframe
Try to block early in the pipeline, from best to worst:
- Prevent request
- Block domain
- Block URL
- Remove part of response
- Change cosmetics
Block domain
cnn.com
# implicitly converted to ||cnn.com^
Block URL
https://news.un.org/zh/story/2019/05/1034202$all
Prevent request
2 approaches: static filter and dynamic filter
- For entities that are meant to be blocked all the time
- The standard way, same as other adblockers
- Can further specify the partiness and entity type
- For entities that are meant to be blocked most of the time
- Easier to test and debug
- Cannot sync/backup with an URL (can sync with uBlock origin server)
Static filter
Address part
This part specifies the server url that hosts the resources
Wildcard:
**is added to the start and the end of the address by default
Exception rule:
@@Start of domain:
||Selecting all subdirectories:
^- Address can end here
- Can only be followed by character like
?or/
Select exact URL: put the URL in a pair of
|
Block option part
This part is optional
- To select asset types:
$ - Asset types:
scriptxmlhttprequestsubdocument(frames)stylesheetimagedomain=(originating domain)
- Inverse:
~
Read more
https://adblockplus.org/filter-cheatsheet
For a more detailed read: https://help.eyeo.com/en/adblockplus/how-to-write-filters
Dynamic filter
- Easy mode: selectively block requests (the best approach)
- Medium mode: block 3rd-party scripts and frames by default. Need to unblock sites by whitelisting their 3rd party scripts
- Hard mode: block all 3rd-party network requests by default
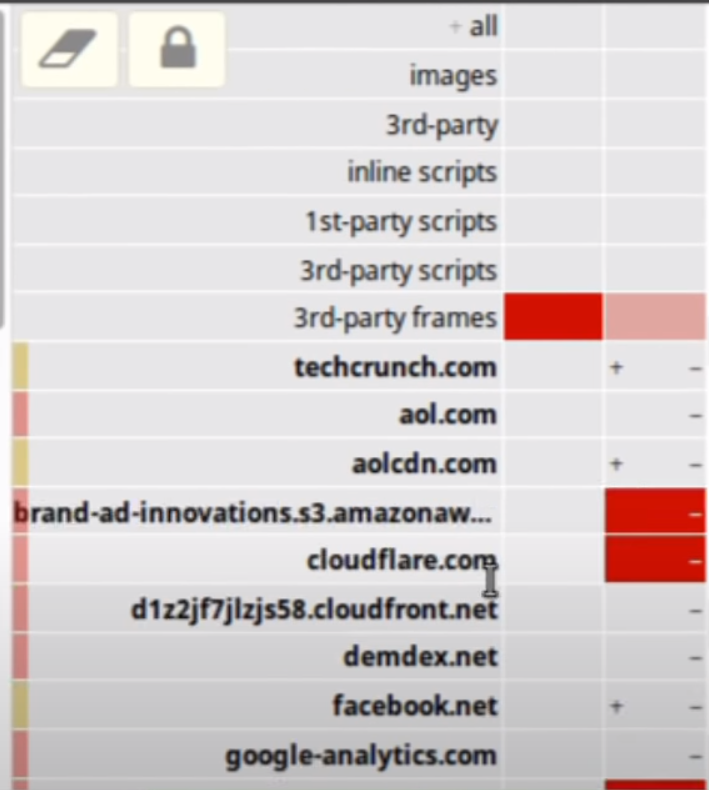
Browser pop-up tool
Guide video: https://www.youtube.com/watch?v=2lisQQmWQkY
Can block any 1st party or 3rd party scripts in the popup window
Left column: global
Right column: local
Color meanings:
- Red: block
- Grey: exception
Reject response
The purpose of HTML filters is to remove elements from a document before it is parsed by the browser.
<domain>##^<body>
- Means removing the element from response html
- Useful for blocking inline scripts and large complex elements
- For Gecko-based browsers only
foo.example##^script:has-text(nuisanceCode)
The above filter means: for any web pages from the foo.example web site, remove all inline script tags which contains the string nuisanceCode.
https://github.com/gorhill/uBlock/wiki/Inline-script-tag-filtering
Example of inline nusance code
Websites use inline scripts and styles to bypass adblockers
// For the content locking
//
//
// When content lock template is shown...
tp.push([
'addHandler',
'showOffer',
offerParams => {
console.log('__PEXP offer', offerParams)
if (offerParams.containerSelector == '.piano-content-lock') {
// ...we add a gradient strip above our template container (it's name should correspond to a specified one in Composer)...
document
.querySelector('.piano-content-lock')
.classList.add('template-shown')
// ...and hide everything after it within the same HTML container (also, the name should be checked)
document
.querySelectorAll('.piano-content-lock ~ *')
.forEach(function (x) {
x.hidden = true
})
// hide the Read More
document.querySelector('.expand').remove()
document.querySelector('.contract').remove()
document.querySelector('.twitter-tweet').remove()
// hide the comments section
document.querySelector('#comment-policy').remove()
document.querySelector('#comment-block').remove()
// expand the content area to include the lock content
var $btext = $('.bigtext')
var currentMiniHeight = $btext.attr('data-miniheight')
// increase content area height by 200 to accomodate the rendered height of the paywall offer
$btext.css(
'height',
parseFloat(currentMiniHeight.slice(0, -2)) + 200 + 'px'
)
}
},
])
// a simpler workaround is to override `overflow: hidden` to `overflow: visible`
<style type="text/css">
.sponsored .page-headline,
.sponsored .storyareawrapper p {
font-family: georgia;
}
.bigtext {
display: block;
overflow: hidden;
color: #787878;
}
.expand, .contract {
cursor: pointer;
font-weight: bold;
padding: 15px 0;
text-align: center;
color: #b00021;
font-size: 20px;
}
.expand:hover, .contract:hover {
color: #555;
}
.hide {
display: none;
}
</style>
Change cosmetics
- To select elements inside iframe, need to write rules regarding the iframe domain
- Strictly in the format
<domain>##<body><domain>is optional, just the domain or subdomain<body>consists of CSS selector followered by a pseudo selector
Pseudo selectors syntax: https://github.com/gorhill/uBlock/wiki/Procedural-cosmetic-filters
:has-text()- No quotes inside
() - Text sensitive
- No quotes inside
:upward():has(): https://github.com/gorhill/uBlock/wiki/Procedural-cosmetic-filters#subjecthasarg:matches-css(arg)is slow and try to avoid- Hiding floating items: they often have
clearfixas part of the classname, becauseclearfixis the hack for floating elements: https://www.w3schools.com/howto/howto_css_clearfix.asp - Advanced features only supported by Gecko-based browsers
:remove():- When hiding the element is not enough, remove the element
- https://github.com/gorhill/uBlock/wiki/Static-filter-syntax#subjectremove
- Change CL: https://github.com/gorhill/uBlock/releases/tag/1.15.0
Hide elements
- Select the element default to hide it
- Can hide popup, large media, iframe directly in browser popup tool
reddit.com##body a
baike789.com##.s-box ul:nth-child(2)
google.com##h3:has-text(Videos):upward(7)
Style elements
Add something like :style(color:red !important;) to the element selector
reddit.com##body a:style(color:red !important;)
https://github.com/uBlockOrigin/uBlock-issues/wiki/Static-filter-syntax#subjectstylearg
Slower approach is to use snippet with
#$#syntax:weather.com#$#.Mobile{height: 100%;width: 100%;position: absolute}
uBlock origin mechanism
Rule list cache
- To purge all remote and local cache, press
shiftwhen clicking "Purge all caches" (keep local cache ifshiftis not pressed) - Default update every 5 days
Inspection order
- Dynamic filters
- HTML filters
- Whitelist
- Url filter
- Static filter
Script injection
- https://github.com/uBlockOrigin/uBlock-issues/wiki/Resources-Library
+js(no-floc): injecting a JavaScript calledno-floc#@#+js(no-floc): user opt-in to FLoC by adding a generic exceptionexample.com,shopping.example#@#+js(no-floc): opt-in only for a specific set of websites through a more specific exception filter
About no-floc
FLoC is a user tracking mechanism by Google (Federated Learning of Cohorts). uBlock filters – Privacy list blocks it by default.